
When we talk about the Internet of Things, we typically think of smart homes and wearable devices. However, with the advent and explosive growth around technologies spurred by the joint all domain command and control (JADC2) initiative comes a new way to apply the IoT to military devices, or IoMT.
Why is JADC2 driving IoMT?
To understand the answer, you first need a quick primer on JADC2. This initiative spans all branches of the U.S. military, seeking to unravel a tangle of interrupted communications, a surge in new devices (unmanned craft are a prime example), and a lack of cohesion in the overall command and control structure. As the military leaps forward in technological advancement to prepare for a shift from counter-insurgency wars to peer-level adversaries, the sheer number of devices is growing rapidly.
AI/ML enters the battlefield
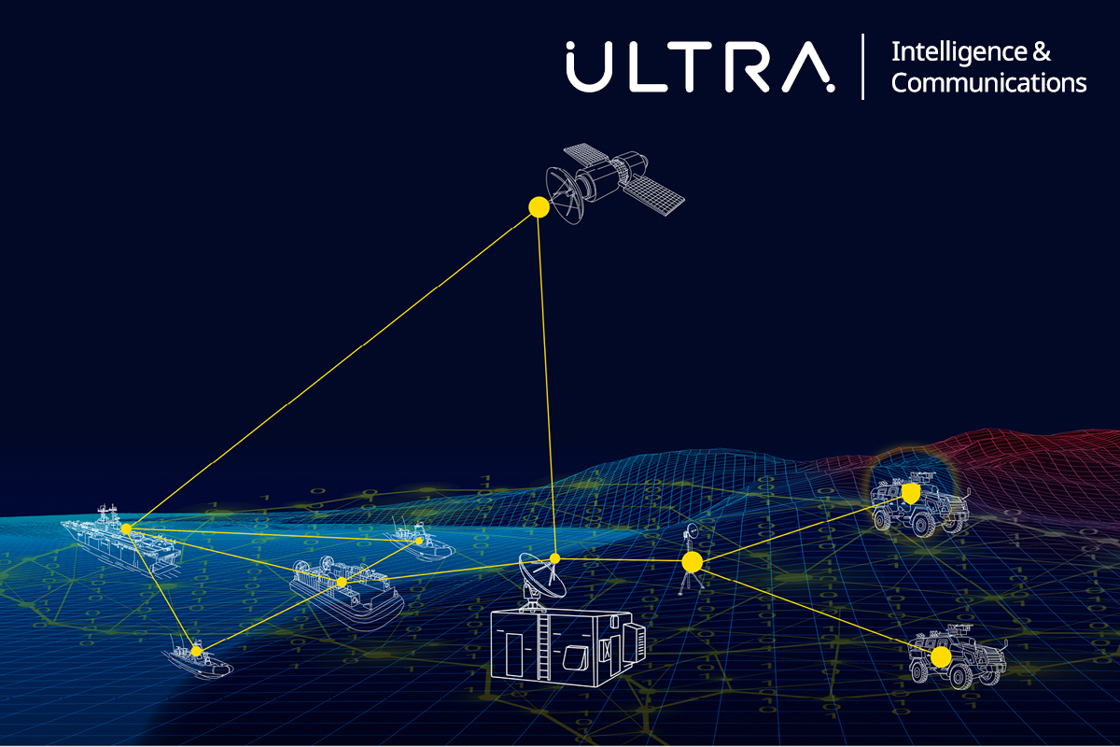
For this initiative to succeed, all the pieces and players on the battlefield must maintain constant communications. The problem is that the overwhelming multitude of sensors and devices produce so much data so quickly that no human could keep up with it. This sets the stage for AI/ML to step in and monitor data, surfacing only that data required by the mission – a technology evolving quickly into prototype, testing and deployment.
Organizations like ReMI are developing next-generation practical applications for using AI/ML across the whole of the IoMT via breakthroughs like cognitive tactical data networks. These complex networks, to fulfill JADC2 requirements, must establish and maintain communication across all branches of service at all echelons and all relevant communications waveforms and protocols. They must seamlessly integrate these nodes and provide actionable information to commanders at the right place, so they can make the right choice at the right time, providing information advantage.
Aerial bombardment
The skies above the battlefield are also increasingly crowded. With the advent of unmanned devices ranging from tiny intelligence-gathering drones to smart missiles, the IoMT has further complicated the command-and-control (C2) structure. Not all complications are bad, however, and the wealth of opportunities for data gathering and tracking enemy movements makes C2 more powerful and effective than ever.
How do commanders and their staff even track these devices? They need to be tuned in to the flood of data resulting from the IoMT. Software that tracks all the aerial players must accommodate thousands of tracks (or disparate devices) to provide an accurate picture.
The future of aerial devices, manned and unmanned, again hinges on the development and deployment of a cognitive framework while maintaining the safety net of a “human the loop .” As JADC2 demands inter-branch coordination, the solution must also take into account aircraft from the Air Force, Navy, Marines and Army, as well as an adversary’s assets and capabilities. Only when Allied forces have a clear picture of the battle space and the ability for real-time decision making can we hope to effectively combat peer and near-peer threats.
Incorporating soldier-borne devices
Soldier-borne IoMT sensors run the gamut from intelligence-gathering to wearable biometrics that monitor a warfighter’s health and mental state. These specific subsets are often referred to as the Internet of Battlefield Things (IoBT). When you begin to include this data from every single warfighter, you can again become overwhelmed. It isn’t practical to expect an analyst to pick out that a soldier’s heartrate is dangerously low, or that a group of friendly combatants has run into a pocket of resistance and requires backup.
The IoMT/IoBT must rely upon a network that can communicate only relevant data back to C2. This line of communication must not be compromised, or it could result in substantial losses.
A cautionary tale
In the fall of 2020, U.S. forces engaged in a massive exercise that simulated a battle for Taiwan. The U.S. was defeated in a matter of moments. Several factors contributed to this loss, but chief among them was the loss of vital communications. Nation-state operatives gained control of U.S. comms and that was, as they say, all she wrote. Without the ability to communicate effectively, our forces shut down and were handily overcome.
Why did the U.S. lose this wargame, and why so quickly? Put simply, it was because we conducted the battle in the same way we’ve done for 20 to 30 years. The enemy has had ample time to deconstruct our strategies and to learn how to use that knowledge to essentially hack our comms and create utter chaos. A force that cannot communicate cannot win.
JADC2 aims to put an end to exactly this kind of attack by protecting communications between all branches with an array of tools that will secure networks. When we say “secure,” we mean “essentially impenetrable.” Considering that the U.S. employed the same strategies, it is imperative to introduce real technical differentiators via technologies like the IoMT and other secure initiatives like the introduction of AI/ML to defeat and deceive jammers.
Tomorrow is closer than you think
At Ultra, we are investing heavily in the future of JADC2, and with that comes a substantial investment in the IoMT. Our cognitive capabilities under development encompass everything from self-healing and anti-jamming tactical datalink networks to air defense systems that can track up to 16,000 vehicles to hardened and proven secure mesh networks to defend the IoMT edge and all points between.
As we ponder and prepare for eventual peer-level conflicts, we cannot disregard the impact of JADC2’s integration and the need to provide real-time decision making in the heat of the moment. “Integrated” cannot be a simple buzzword – it must have meaning in the field where the capability is needed most.
Relevant links
Ultra’s Cognitive Tactical Network
